Users
This page describes the user's roles and permissions, and the authorized operations allowed on each permission level.
Roles and Associated Permissions
The following table describes the relationships between the user types and their common roles:
Role Type | Level 1 | Level 2 |
|---|---|---|
Merchant Management | Merchant Admin:
| |
Customer Service | Merchant Customer Service (lower-level CS role):
| Merchant CS Admin (highest-level CS role)
|
Operations | Hub Operator Comment: (lowest-level Hub role):
| Hub Admin (highest-level Hub role) |
Note
If you are creating or replicating an internal Global-e employee's permissions, view another Global-e user’s setup and copy it.
User Roles
The following table describes the user roles:
Users | Common Role Combinations |
|---|---|
Full Merchant Permissions | Merchant Admin + Merchant CS Admin + Hub Admin ( +Store Roles If Applicable) |
Hub Processor (Merchant’s Own Warehouse Team) | Merchant Admin + Hub Admin |
Hub Processor (3PL Team’s Lead) | Hub Admin |
Hub Processor (3PL Team) | Hub Processor |
CS Lead | Merchant Admin + Merchant CS Admin |
CS Team | Merchant Admin + Merchant CS |
Merchant Portal Roles and Permissions
Menu Item | Page | Sub Page | Actions | Merchant CS | Merchant CS Admin | Merchant Admin | Hub Admin | Hub Operator |
Orders | √ | √ | X | X | X | |||
View Orders | √ | √ | X | X | X | |||
Search Bar | √ | √ | X | X | X | |||
Search for orders | √ | √ | X | X | X | |||
General tab | Display Invoice | √ | √ | X | X | X | ||
Display Printed Documents | √ | √ | X | X | X | |||
Create Return | √ | √ | X | X | X | |||
Cancel Order | X | √ | X | X | X | |||
Export Order list | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
View Documents | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
√ | √ | X | X | X | ||||
Edit Merchant Order Id | √ | √ | X | X | X | |||
Edit Merchant Internal Order Id | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
√ | √ | X | X | X | ||||
Add an Order Comment | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
Amend Order Products | X | √ | X | X | X | |||
Create a replacement | X | √ | X | X | X | |||
Refunds Tab | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
Create a Refund | X | √ | X | X | X | |||
Delivery Tab | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
√ | √ | X | X | X | ||||
√ | √ | X | X | X | ||||
√ | √ | X | X | X | ||||
Shipping & Billing | √ | √ | X | X | X | |||
√ | √ | X | X | X | ||||
√ | √ | X | X | X | ||||
Edit Shipping Address | X | √ | X | X | X | |||
Save edited address | X | √ | X | X | X | |||
Returns | √ | √ | X | X | X | |||
Search for orders | √ | √ | X | X | X | |||
Open RMA screen | √ | √ | X | X | X | |||
Add Return notes | √ | √ | X | X | X | |||
Global‑e Hub | X | X | X | √ | X | |||
Process Orders | X | X | X | √ | X | |||
Search for an order | X | X | X | √ | X | |||
Process Order | X | X | X | √ | X | |||
Place on Hold | X | X | X | √ | X | |||
Reprint Order | X | X | X | √ | X | |||
Process Returns | X | X | X | √ | X | |||
Process Return | X | X | X | √ | X | |||
Process EOD | X | X | X | √ | X | |||
Process EOD for hubs | X | X | X | √ | X | |||
View older manifests | X | X | X | √ | X | |||
Process PUDO EOD | X | X | X | √ | X | |||
Process EOD for hubs | X | X | X | √ | X | |||
View older manifests | X | X | X | √ | X | |||
Process Stores EOD | X | X | X | √ | X | |||
Process EOD for hubs | X | X | X | √ | X | |||
View older manifests | X | X | X | √ | X | |||
Process Returns EOD | X | X | X | √ | X | |||
X | X | X | √ | X | ||||
Select Hub | X | X | X | √ | X | |||
Process EOD for hubs | X | X | X | √ | X | |||
View older manifests | X | X | X | √ | X | |||
PUDO Distribution | X | X | X | √ | X | |||
Process EOD for hubs | X | X | X | √ | X | |||
View older manifests | X | X | X | √ | X | |||
Stores Distribution | X | X | X | √ | X | |||
Filer orders | X | X | X | √ | X | |||
Merchant Hub | X | √ | X | √ | √ | |||
Process Orders | X | X | X | √ | √ | |||
X | X | X | √ | √ | ||||
Bulk Process Orders | X | X | X | √ | √ | |||
Process orders | X | X | X | √ | √ | |||
Export to Excel | X | X | X | √ | √ | |||
Print Orders | X | X | X | √ | √ | |||
Process EOD | X | X | X | √ | √ | |||
Process EOD for hubs | X | X | X | √ | √ | |||
View older manifests | X | X | X | √ | √ | |||
Process Orders: Non GE Carriers | X | √ | X | √ | X | |||
Process orders | X | √ | X | √ | X | |||
View Process Orders | X | X | X | √ | X | |||
Reprint Labels | X | X | X | √ | X | |||
Reprint in bulk | X | X | X | √ | X | |||
Canceled Orders | X | X | X | √ | X | |||
Reprint Labels | X | X | X | √ | X | |||
View order info | X | X | X | √ | X | |||
Failed Transfer to Merchant | X | √ | X | √ | X | |||
Resend Orders | X | √ | X | √ | X | |||
Resend in Bulk | X | √ | X | √ | X | |||
Failed Orders | X | X | X | √ | X | |||
Reprint Labels | X | X | X | √ | X | |||
Pickup Request | √ | √ | X | √ | √ | |||
Select Hub | √ | √ | X | √ | √ | |||
Select Merchant | √ | √ | X | √ | √ | |||
Request a Pickup | √ | √ | X | √ | √ | |||
Same Day Dispatch Orders | √ | √ | X | √ | √ | |||
Mark as Received in Hub | √ | √ | X | √ | √ | |||
System | X | √ | X | √ | X | |||
Users | X | √ | X | √ | X | |||
Search for users | X | √ | X | √ | X | |||
Edit User | X | √ | X | √ | X | |||
Merchants | X | √ | X | X | X | |||
Product Management | X | √ | X | X | X | |||
Restricted Products | X | √ | X | X | X | |||
Search for a product | X | √ | X | X | X | |||
Upload product list | X | √ | X | X | X | |||
Restrict a product | X | √ | X | X | X | |||
Remove restriction | X | √ | X | X | X | |||
Product Price Feed | X | √ | X | X | X | |||
Upload a list | X | √ | X | X | X | |||
Configure the list | X | √ | X | X | X | |||
Generate a feed | X | √ | X | X | X | |||
Configuration | X | X | √ | X | X | |||
Marketing Proposition | X | X | √ | X | X | |||
Marketing Proposition | X | X | √ | X | X | |||
X | X | √ | X | X | ||||
X | X | √ | X | X | ||||
Select a merchant | X | X | √ | X | X | |||
Edit shipping rates | X | X | √ | X | X | |||
Edit Country Coefficient | X | X | √ | X | X | |||
Save changes | X | X | √ | X | X | |||
Campaign | X | X | √ | X | X | |||
X | X | √ | X | X | ||||
Add campaign | X | X | √ | X | X | |||
Save changes | X | X | √ | X | X | |||
Returns | X | X | √ | X | X | |||
X | X | √ | X | X | ||||
Edit rates | X | X | √ | X | X | |||
Change History | X | X | √ | X | X | |||
X | X | √ | X | X | ||||
Search per date | X | X | √ | X | X |
Users Management
This section applies to the Store Admin. As the Admin, you can create new users for Merchant stores with which the Merchant is associated in the Global‑e system. You can also edit these users.
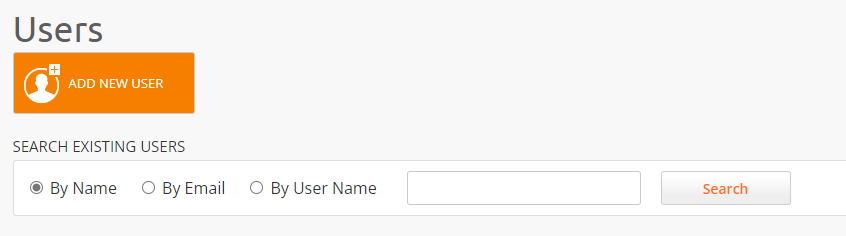
User Management Main Screen
Searching Users
From here you can search existing users, including those that you've just added.
Navigate to System > Users from the top menu.
Select one of the following parameters:
By Name
By Email
By User Name
Type the information according to your selection in Step 2 in the field to the right, and click Search.
A screen is displayed showing the following user information (if defined):
First name
Last name
Email
Assigned roles
User name
IP of last login
Status
Cell phone number
Fax number
Phone number
Adding a New User
From here you can add new users into the Global-e platform. Note that you need admin permissions to add or edit users.
Click ADD NEW USER.
Provide the required information from the ADD NEW USER panel,
Assign the required roles:
Merchant Admin
Hub Admin
Hub Operator
Click Save.
Editing Users
This page describes how to edit existing users.
The following users can edit existing users:
Global admins
Merchant, CS, and Hub admins with adequate permissions for the specific feature.
For more information, see Merchant Portal Roles and Permissions.
Search for a user in the Search field, that you need to edit.
Select one of the following:
By Name
By Email
By User Name
Type the relevant information in the search field, based on your selection above
Click Search.
The user is displayed in the search results area.
Click Edit User at the end of the row.
The Edit User screen is displayed.
Edit the fields as required, including:
Personal information
Add, remove, or change roles as required
Click Reset Password to reset your password
Click Save.
Blocking and Unblocking Users
Users with Admin permissions can block or unblock users by clicking  (block) or
(block) or  (unblock).
(unblock).
SSO Integration
Introduction
As part of its solution, Global‑e supports single sign-on with SAML web authentication.
Security Assertion Markup Language (SAML) is an open standard that allows identity providers (IdP) to pass authorisation credentials to service providers (SP).
SAML is mostly used as a secured web-based authentication mechanism as it relies on using the browser agent to broker the authentication flow. Global‑e plays the role of Service Provider and implements the ServiceProvider-initiated SSO SAML flow.
For more info on SAML, see: https://developer.okta.com/docs/concepts/saml/
This document targets the Merchant’s IT personnel or Integrator in charge of performing the SSO integration between the Merchant IdP system and Global-e Merchant Portal.
Note
The end-user (or user) represents the designated Merchant personnel with permission to use the Global‑e Merchant Portal. This could be, for example, a Merchant Admin, Store User, Store Admin, and more.
General Information
Service Provider Initiated Flow
As the Service Provider (SP), Global‑e initiates the sign-on flow, as illustrated in the following Service Provider Initiated Flow figure.
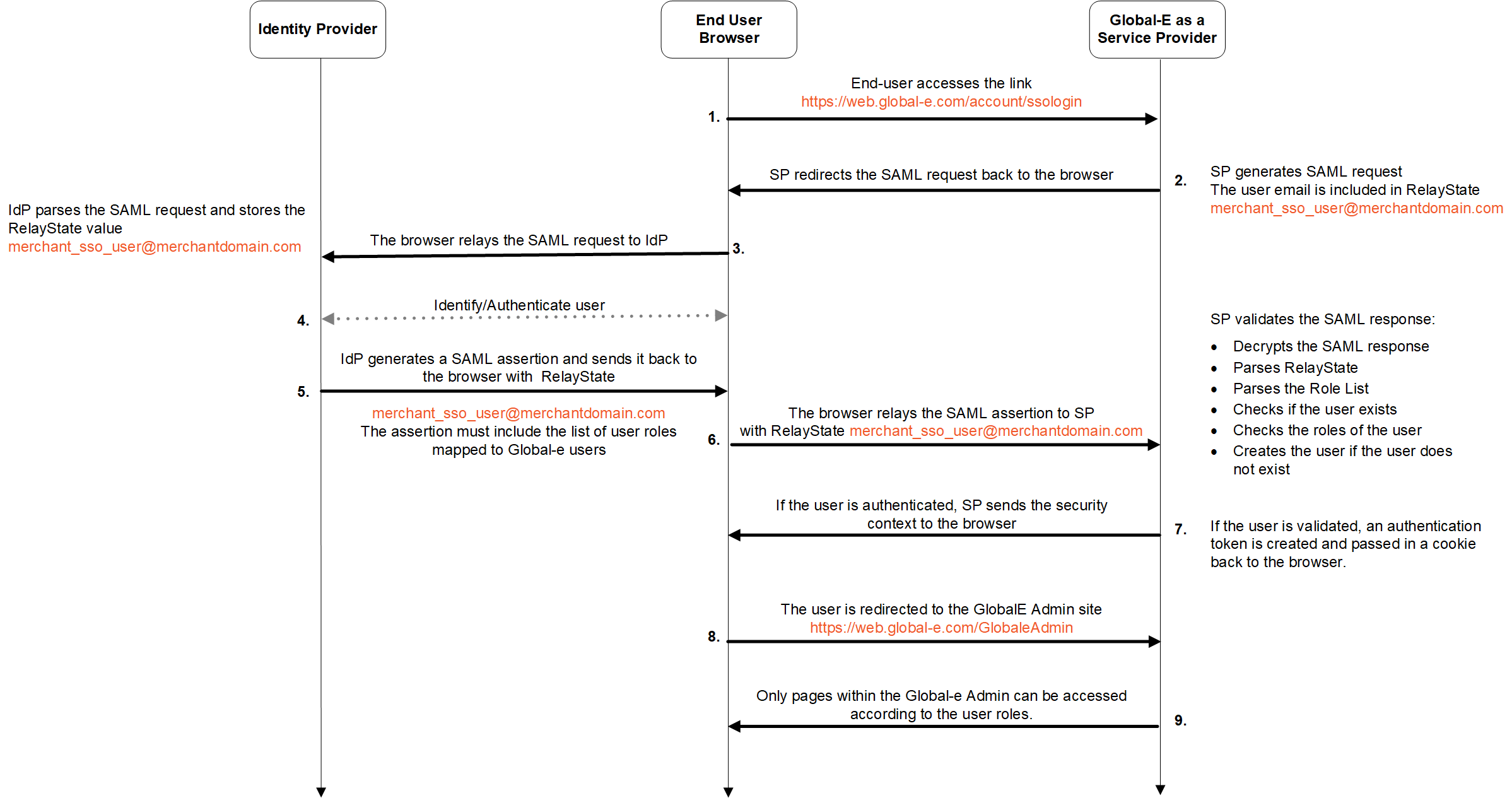 |
Flow:
The end-user accesses the Global‑e Merchant Portal and enters only their employee email address:
Global‑e Merchant Portal URL: https://web.global-e.com/account/ssologin
Merchant employee email example:
See Screens: Accessing the Global‑e Service Provider.
Global‑e SP generates a SAML request together with the employee’s email included in
RelayState.
The Global‑e SP initiates a SAML redirect to the end-user web browser. This means that when the user clicks login, the user is redirected to the Identity Provider sign-in page and prompted to enter the username and password.
The end-user browser relays the SAML request to the Identity Provider (IdP).
IdP identifies and authenticates the user: IdP parses the SAML request IdP stores the
RelayStatevalue (user email address).IdP generates a SAML assertion (XML document containing the userauthorisation ) and returns it with the user's email address to the user's browser. The assertion document must include the required list of roles supported by the Global- Merchant Portal. See Configuring User Roles.
The user browser returns the SAML assertion to the Global-e SP together with the user email.
Global‑e SP validates the SAML response:
Decrypts the SAML response
Parses the
RelayStateParses the Role List (see Role List)
Checks if the user exists by searching for the user e-mail received in
RelayStateas part of the SAML response.Checks the roles of the user
Creates the user if the user does not exist
If the user is validated, Global‑e SP creates an authentication token and passes it in a cookie to the user's browser.
The user is redirected to the Global-e Merchant Portal: https://web.global-e.com/GlobaleAdmin.
Global‑e pages are accessible based on user role.
User Interface
The user accesses the Global-e Merchant Portal by entering only their employee email address (merchant domain).
Example: [email protected]
Accessing the Global‑e Service Provider (Global‑e SP)
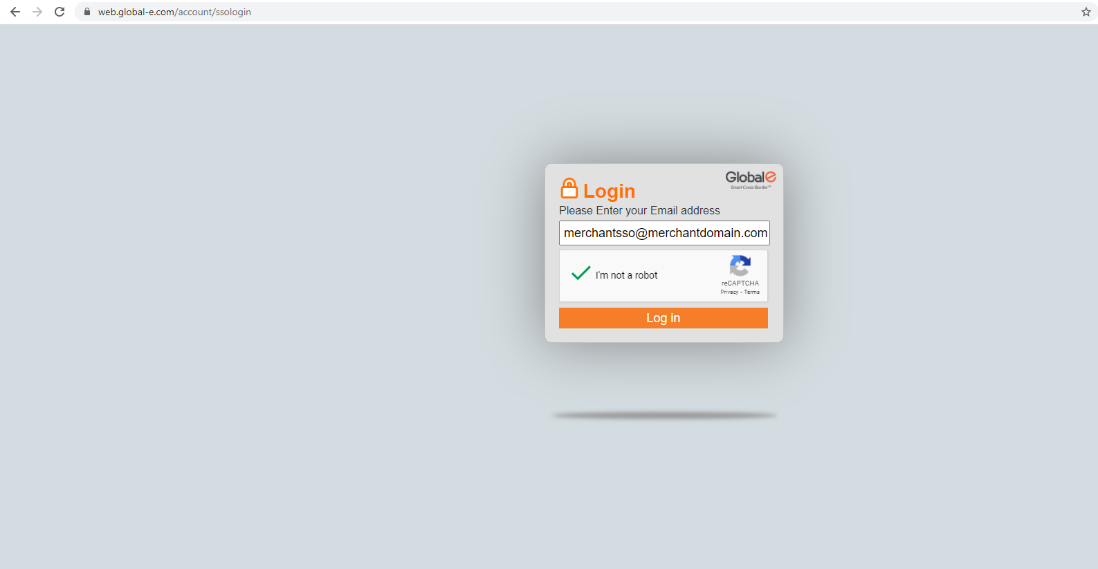
When the user clicks login, Global-e redirects them to the IdP Sign-in page (see IdP Sign-in and Authentication Example below), where they enter user credentials (email and password). IdP identifies and authenticates the user before granting access to the Global-e Merchant Portal based on user role.
IIdP Sign-in and Authentication (Example)
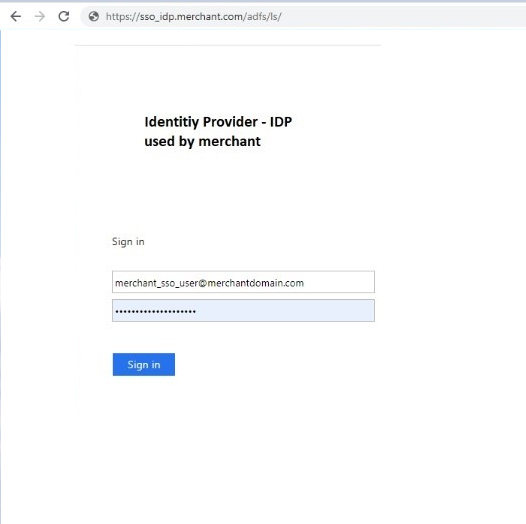
Accessing the Global‑e Merchant Portal

Supported Binding
Global‑e SP supports HttpGet and HttpPost binding for the single sign-on.
Global‑e Identifier
The Identifier allows the Merchant’s IdP to identify Global‑e as a Service Provider.
This Global-e SP entity identifier is a fixed value represented as follows:
PROD (Production):
9c41258e-0c9d-43b4-ba15-242b139011fd
STG (Staging):
0d1821aa-309a-4314-b5fe-b4a7c3debbe8
INT (Internal):
0d1821aa-309a-4314-b5fe-b4a7c3debbe8
Example:
The following SAML request XML attribute specifies the Global‑e SP entity identifier:
entityID=https://wwww.global-e.com/9c41258e-0c9d-43b4-ba15-242b139011fd
Metadata
SAML supports metadata endpoint link exchange between IdP and SP, where IdP provides the Global‑e SP with the link to the XML publicly available metadata and vice versa. This simplifies the setup process.
One way to configure such a relationship is to exchange metadata files between the SP side and IdP via metadata links, where the SP side can receive an IdP metadata file and generate an SP metadata file for consumption by IdP.
Global‑e Metadata
Global‑e SP exposes SAML metadata either via a link or via a file that can be downloaded from the link.
The Global‑e metadata includes the following parameters:
The SP entity id
An endpoint to redirect the end user for
HttpGetbinding:PROD (Production): https://secure.global-e.com/account/externallogin
STG (Staging): https://secure2.bglobale.com/account/externallogin
INT (Integration): https://secure.bglobale.com/account/externallogin
An endpoint to redirect the end user for
HttpPostbinding:PROD (Production): https://secure.global-e.com/account/externallogin
STG (Staging): https://secure2.bglobale.com/account/externallogin
INT (Integration): https://secure.bglobale.com/account/externallogin
A public certificate and signature for signing and encryption
Global‑e contact details
Note
Contact Global‑e if you are not sure whether to use the values for PROD, STG, or INT.
IdP Metadata
Global‑e gets the IdP metadata by accessing the link sent by IdP.
The IdP metadata initiates a SAML request.
The IdP metadata includes:
An IdP redirect URL (for SAML Request)
A IssuerID
An IdP logout endpoint link
A public certificate and a signature for signing and encryption
Endpoints
The Global‑e SP metadata is accessible either through the URL or via a file available for download. This metadata provides IdP with the necessary information to communicate with Global‑e.
To access the Global-e SP Metadata:
Example of Global‑e SP Metadata:
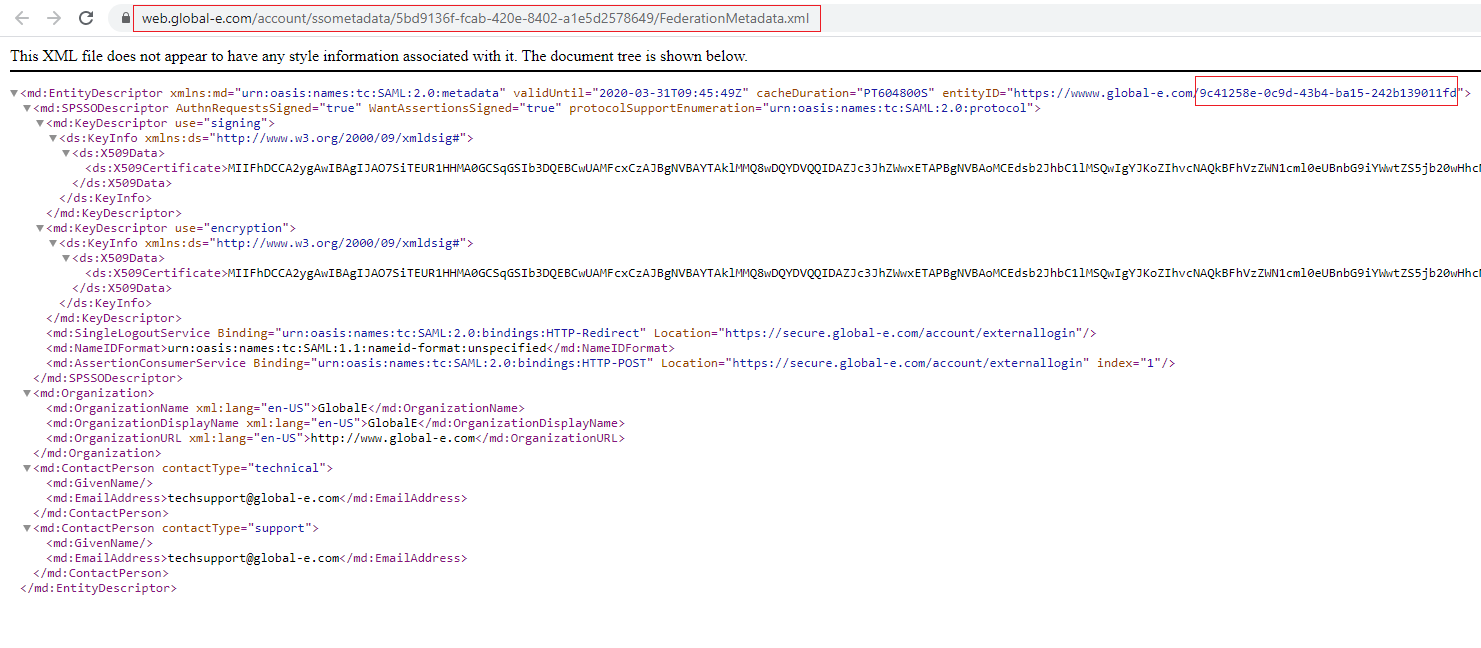
To Download the Global-e SP Metadata File:
SAML Response
IdP transfers the SAML response to the Global‑e SP endpoint that supports both HttpGet and HttpPost SAML bindings: https://secure.global-e.com/account/externallogin
Integrating Global‑e SP with IdP
This section details the steps required to register Global-e as a trusted entity within IdP.
To integrate Global-e SP with IdP:
Register the Global‑e SP entity in IdP using the metadata endpoint links exchange method. See Metadata.
In IdP, configure the list of user roles supported by Global‑e SP. See Configuring User Roles.
Register IdP in Global‑e SP using the metadata endpoint links exchange method. See Metadata.
Global‑e maps the Merchant user roles in the Global‑e system.
Configuring User Roles
To configure the list of user roles:
Prepare the list of employees (users) that should have permission to use the Global‑e Admin.
Associate each user to one or several roles supported by Global‑e SP (see list of supported roles further below).
Provide this list of SSO users and associated roles to the Identity Provider so that they can configure and include these roles in the SAML response to be sent to Global‑e.
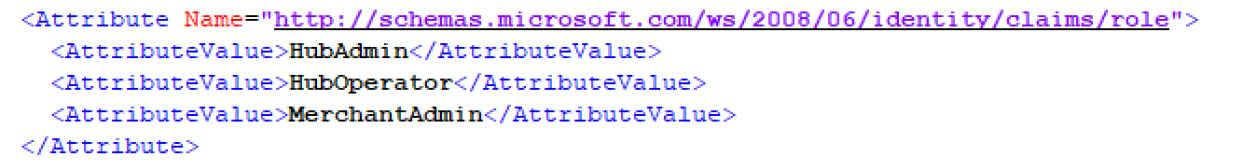
Global‑e supports the following roles:
1. HubAdmin
2. HubOperator
3. MerchantAdmin
4. MerchantCS
5. MerchantCSAdmin
6. StoreAdmin
7. StoreUser
In the IdP SAML response to Global‑e, Global‑e SP expects to get the list of SSO users associated with the roles supported by Global‑e SP, as illustrated in the following section.
Configuring Merchant Domains
If you have more than one domain, send us the list of addresses of all the domains for which you want SSO support so that Global‑e can set this up.
Example of SAML Communication between Global‑e SP and IDP
Example of SAML Response with Linked Roles - Sent by IdP to Global‑e
Example of SAML Request - Sent by Global‑e SP to IdP
<?xml version="1.0" encoding="UTF-8"?>
<samlp:AuthnRequest
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
ID="pfxfb6ffca7-86f9-48c3-9c43-bde99801a526"
Version="2.0"
IssueInstant="2004-12-05T09:21:59Z"
Destination="https://login.microsoftonline.com/951e7c97-7cdd-4af6-a822-c9482cae5056/saml2"
AssertionConsumerService="https://securedev.bglobale.com/account/externallogin"
AttributeConsumingServiceIndex="0">
<saml:Issuer>https://wwww.global-e.com/5f4f1908-c9e8-4617-ace7-7d8f44e490d6</saml:Issuer>
<samlp:NameIDPolicy
AllowCreate="true"
Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient"/>
</samlp:AuthnRequest><?xml version="1.0" encoding="UTF-8"?>
Example of SAML Response – Sent by IdP to Global‑e SP
<?xml version="1.0" encoding="UTF-8"?>
<samlp:Response ID="_a225292d-cf07-43d8-83df-9246165ace4e" Version="2.0" IssueInstant="2021-01-11T18:47:39.327Z" Destination="https://secure-qa.bglobale.com/account/externallogin" InResponseTo="pfxf9c319d6-6797-452e-887b-5a3dcccf4ebc" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://sts.windows.net/951e7c97-7cdd-4af6-a822-c9482cae5056/</Issuer>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</samlp:Status>
<Assertion ID="_2903b71e-4f90-4b5d-9156-b83de9b24c00" IssueInstant="2021-01-11T18:47:39.327Z" Version="2.0" xmlns="urn:oasis:names:tc:SAML:2.0:assertion">
<Issuer>https://sts.windows.net/951e7c97-7cdd-4af6-a822-c9482cae5056/</Issuer>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
<Reference URI="#_2903b71e-4f90-4b5d-9156-b83de9b24c00">
<Transforms>
<Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</Transforms>
<DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<DigestValue>4VWqR0pUrTvBE8FVoOO3D8VFUNAIRHLePqpePWZJxKU=</DigestValue>
</Reference>
</SignedInfo>
<SignatureValue>YCCkRSk0UduDisy4oZxD3v0qGM1wgd36Fg5FXtiL5pENNIcisYdDRquvjy4fNURXhNBMt1HoAeN9jDY8hcamw517X3lJk3imGiDhKT9yIB7VSjPS4azLDqym+uL48vuoUSXfRoaA9TYrLQMhWTn8U0KTB6M/PZlh+2aUSRyxAJiW8zdTNGeDAJM6ICgecQ0Z+wx1BZW6VmBRtH74VpSq3OXcF/1igZnkNRljhr5oKdLdtjJsENhthH1cCGq9q6igZLwalCZesTXCOjK0zO+iJSk7i4kh21X8314x/a6u5tjLr2OkMKP9ChwI1d+cfDe3YLRNvR7ipFGEP6vMR1w/LQ==</SignatureValue>
<KeyInfo>
<X509Data>
<X509Certificate>MIIC8DCCAdigAwIBAgIQEnS+YGZcgbxJ8hPIMskBvzANBgkqhkiG9w0BAQsFADA0MTIwMAYDVQQDEylNaWNyb3NvZnQgQXp1cmUgRmVkZXJhdGVkIFNTTyBDZXJ0aWZpY2F0ZTAeFw0yMDA0MjYxNTA4MDJaFw0yMzA0MjYxNTA4MDJaMDQxMjAwBgNVBAMTKU1pY3Jvc29mdCBBenVyZSBGZWRlcmF0ZWQgU1NPIENlcnRpZmljYXRlMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA1pukQAAW/qMeMMsD9LZiGwkRpv05y8GSuDx8hnkb5j2Ne+jL5DwAuZhpQAjVtLrMWww+CsScqOSRuXdZvQHzmPgxiD6ZoLxyZsG/EIcjTK80Sb3jruTW87x7Aci873STY0knfGoDfWnJF3QhRYXw0XJpT/1HMXBqnhVY/AzQZWkG70fQW4Hw1+RSTqSetY+Ju72/mR14JQg0eqXnYtpDyJV05JZHlpJ7mFpQVtLg2b9YhkGj/DItQAkvU8e9fuf3jNnPKAOVMPWfoWcbiq/Dyh5TnpNe/9zkruG46pS6eAyNOUyeYv3Vr5ZAw98/q9jJM/LaFn0KYVM5BMtcYDI6mQIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQC01f16JITMAbLwXyYNU8y41YoHcNBbETESKhOlP6zT/zxH2k2XCap4WyXwdrUqFIA0mP/HKgdDdN4KiFUj3nXPXYSZaxjXqlrLRYMTJE4LKZ8iBdAEJ3OjJOA48guNPU+rsoCPTUX+74YOQ3w3XyDhKOWhNjj2fzaFEU6aaGOnHh6s6PHPgQL8uoXYhg6pMQ10m9PtPK12PY6RL+v9HuuRGb+itW1rarlAVS5EPCVxntnDTCv9UUXnEwyQmYp9tmMpkFBpSwjZmwK1BTrUhieJRutwCAM/jQ5cGNAVozr4bx8OV0+25Gd5+f6PIdddyeHCwCIn6wPlV6gwmQCqBzKC</X509Certificate>
</X509Data>
</KeyInfo>
</Signature>
<Subject>
<NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient">C1Y5LlgRS2Ms1wmUwkA8W5zCu6Q30w93nuMb5rL06RY=</NameID>
<SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<SubjectConfirmationData InResponseTo="pfxf9c319d6-6797-452e-887b-5a3dcccf4ebc" NotOnOrAfter="2021-01-11T19:47:38.951Z" Recipient="https://secure-qa.bglobale.com/account/externallogin" />
</SubjectConfirmation>
</Subject>
<Conditions NotBefore="2021-01-11T18:42:38.951Z" NotOnOrAfter="2021-01-11T19:47:38.951Z">
<AudienceRestriction>
<Audience>https://wwww.global-e.com/5f4f1908-c9e8-4617-ace7-7d8f44e490d6</Audience>
</AudienceRestriction>
</Conditions>
<AttributeStatement>
<Attribute Name="http://schemas.microsoft.com/identity/claims/tenantid">
<AttributeValue>951e7c97-7cdd-4af6-a822-c9482cae5056</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/identity/claims/objectidentifier">
<AttributeValue>44036fae-af4f-4a18-bd14-dfc7de1487fd</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/identity/claims/displayname">
<AttributeValue>SSO01</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/identity/claims/identityprovider">
<AttributeValue>https://sts.windows.net/951e7c97-7cdd-4af6-a822-c9482cae5056/</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/claims/authnmethodsreferences">
<AttributeValue>http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/role">
<AttributeValue>HubAdmin</AttributeValue>
<AttributeValue>HubOperator</AttributeValue>
<AttributeValue>MerchantAdmin</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname">
<AttributeValue>SSO</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname">
<AttributeValue>User</AttributeValue>
</Attribute>
<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name">
<AttributeValue>[email protected]</AttributeValue>
</Attribute>
</AttributeStatement>
<AuthnStatement AuthnInstant="2021-01-11T18:46:02.700Z" SessionIndex="_2903b71e-4f90-4b5d-9156-b83de9b24c00">
<AuthnContext>
<AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClassRef>
</AuthnContext>
</AuthnStatement>
</Assertion>
</samlp:Response>Checklist of Items to Send to Global‑e
Make sure to send the following items to Global‑e to ensure adequate setup and support:
Identity provider metadata URL.
Example URL:
Note the
appidparameter at the end of the URL.SAML2 binding type - HttpPost or HttpRedirect
Allowed roles for SSO users. Only users with these roles are allowed to log in as SSO. Contact Global‑e if you require additional roles.
The list of all your domains that require SSO support.
A test user account and credentials for Global‑e for each email domain supporting SSO (for testing purposes).
Note
If you have a separate sandbox working with the Global‑e Staging environment, make sure to provide this information for both, your sandbox, and your production website.